Cybersecurity planning and preparedness are essential. No single solution or software can guarantee complete immunity from data breaches in today’s complex technological landscape and, while one-time software deployment may lessen exposure, it does not offer long-term security solutions or accurate privacy compliance. Organizations do not often possess large resources to support ever-evolving cybersecurity needs, hence cybersecurity strategies must be carefully designed and addressed efficiently.
The PrivacyRules Cybersecurity Services offers to any organization the opportunity to develop its own customized cybersecurity process. Our global horizontal alliance of cybersecurity firms cooperates in a non-competitive ecosystem to provide clients with strategic consulting and a solid selection of:
- cybersecurity services
-
tailored solutions
-
cutting-edge products
-
cyber awareness and technical training


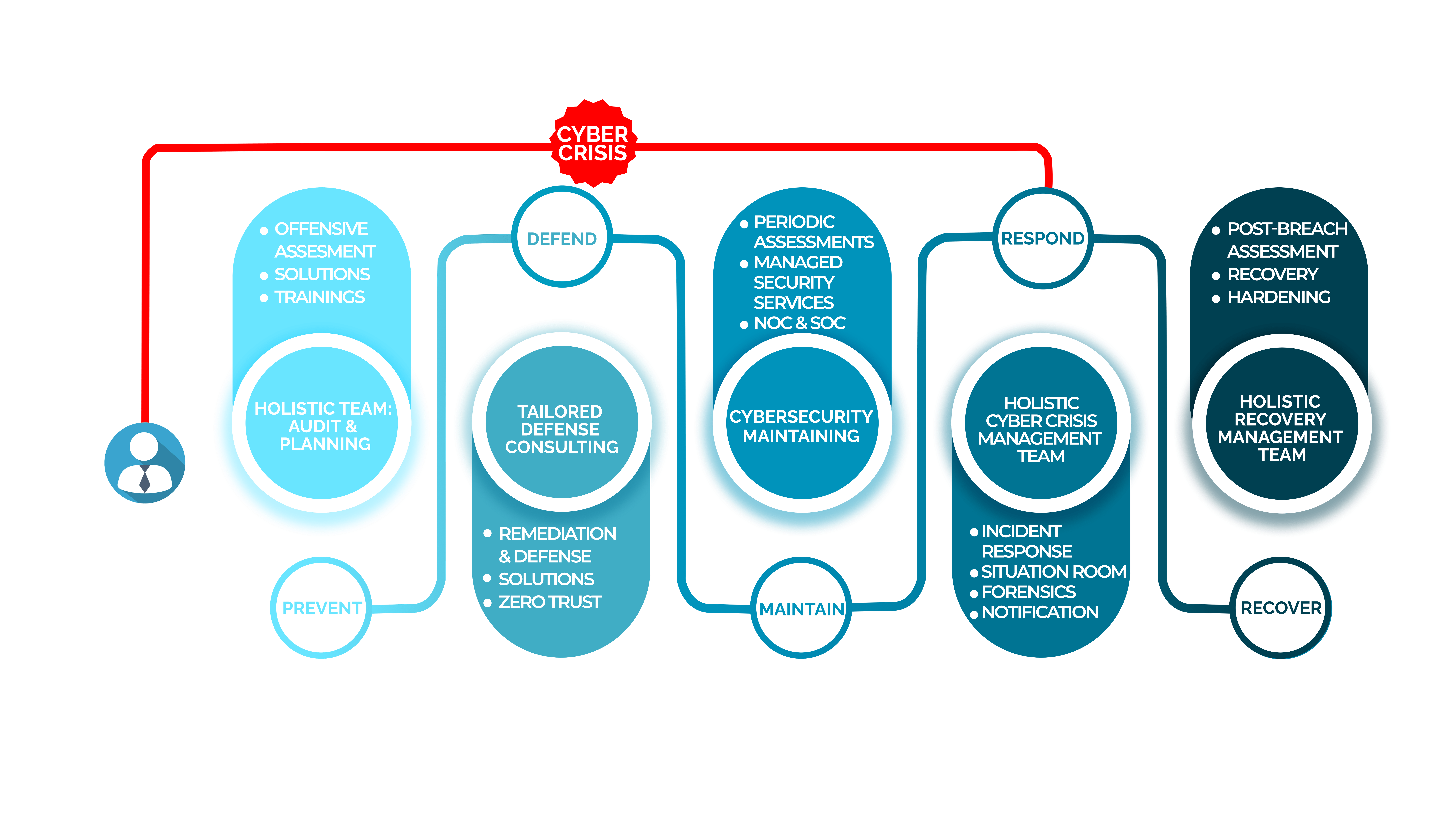
The cybersecurity process is structured along four pillars:
Prevent
Defend & maintain
Respond
Recover


Cybersecurity Services
– Consulting
– Risk Management
– IT Auditing – all types Offensive Security Assessment
– Dedicated R&D Projects
– Proactive Threat Technology
– Enterprise Services
– Removal Blockchain- Zero Trust Technology
– Cyber Defense Consulting & Services
– Biometrical Solutions
– Fraud Prevention
– Identity Protection
– Hardening Countermeasures

– Virus & Malware Protection
– Cyber Threat Intelligence
– Managed Security Services
– Security Operation Centers
– Network Operation Centers
– Rapid Response
– Team Containment & Eradication
– Technical-economic Appraisal
– Technical and Data Recovery Forensics
– Disaster Recovery
– Post Breach Assessment
– Remediation Solutions
– Training
+ More