On Nov. 1, 2021 the China’s Personal Information Protection Law (PIPL) is into effect, aimed to “protect the rights and interests of individuals,” “regulate personal information processing activities,” and “facilitate reasonable use of personal information” (Article 1).
With its entry into force, the broader cyber and data security governance in China is regulated by three pieces of legislation: the PIPL, the Cybersecurity Law, and the Data Security Law. Implementing regulations have been adopted and some have yet to be adopted, making it complex to comply with this framework without proper legal and cybersecurity guidance.
On a comparative perspective, the PIPL aligns with the strictest international privacy benchmarks of the European Union’s General Data Protection Regulation (EU GDPR) in large part, but it differs from the EU framework to a relevant extent. For instance, the PIPL includes certain substantive obligations that differ from the EU GDPR but there are also obligations found in the EU GDPR that are not included in the PIPL.

Impact of the PIPL on companies and entities
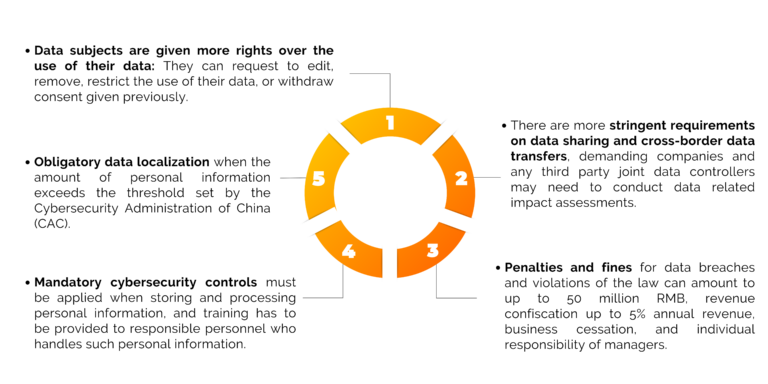
- Data subjects are given more rights over the use of their data: They can request to edit, remove, restrict the use of their data, or withdraw consent given previously.
- There are more stringent requirements on data sharing and cross-border data transfers, demanding companies and any third party joint data controllers may need to conduct data related impact assessments.
- Penalties and fines for data breaches and violations of the law can amount to up to 50 million RMB, revenue confiscation up to 5% annual revenue, business cessation, and individual responsibility of managers.
- Mandatory cybersecurity controls must be applied when storing and processing personal information, and training has to be provided to responsible personnel who handles such personal information.
- Obligatory data localization when the amount of personal information exceeds the threshold set by the Cybersecurity Administration of China (CAC).



New Legal Framework of Data Protection in China
The Cybersecurity Law
- Multi-Level Protection Scheme (“MLPS”) Network Critical Device and Dedicated
- Products Testing and Certification
- Critical Information Infrastructure (“CII”) Security Protection
- Cybersecurity Review
- Cybersecurity Monitoring, Early Warning and Information Notification
The Data Security Law
- Applicable scope: Data processing activities within the territory of the People’s republic of China
- Data Security Standardization System
- Data Security Testing and Evaluation, Certification Administration
- Classified and Graded Data Protection Scheme
- Important Data Catalog
- Data Security Early Warning and Incident Response Scheme
- National Security Review
- Data Transaction and Online-data Processing Activities
- Cross-border Data Transfer Supervision
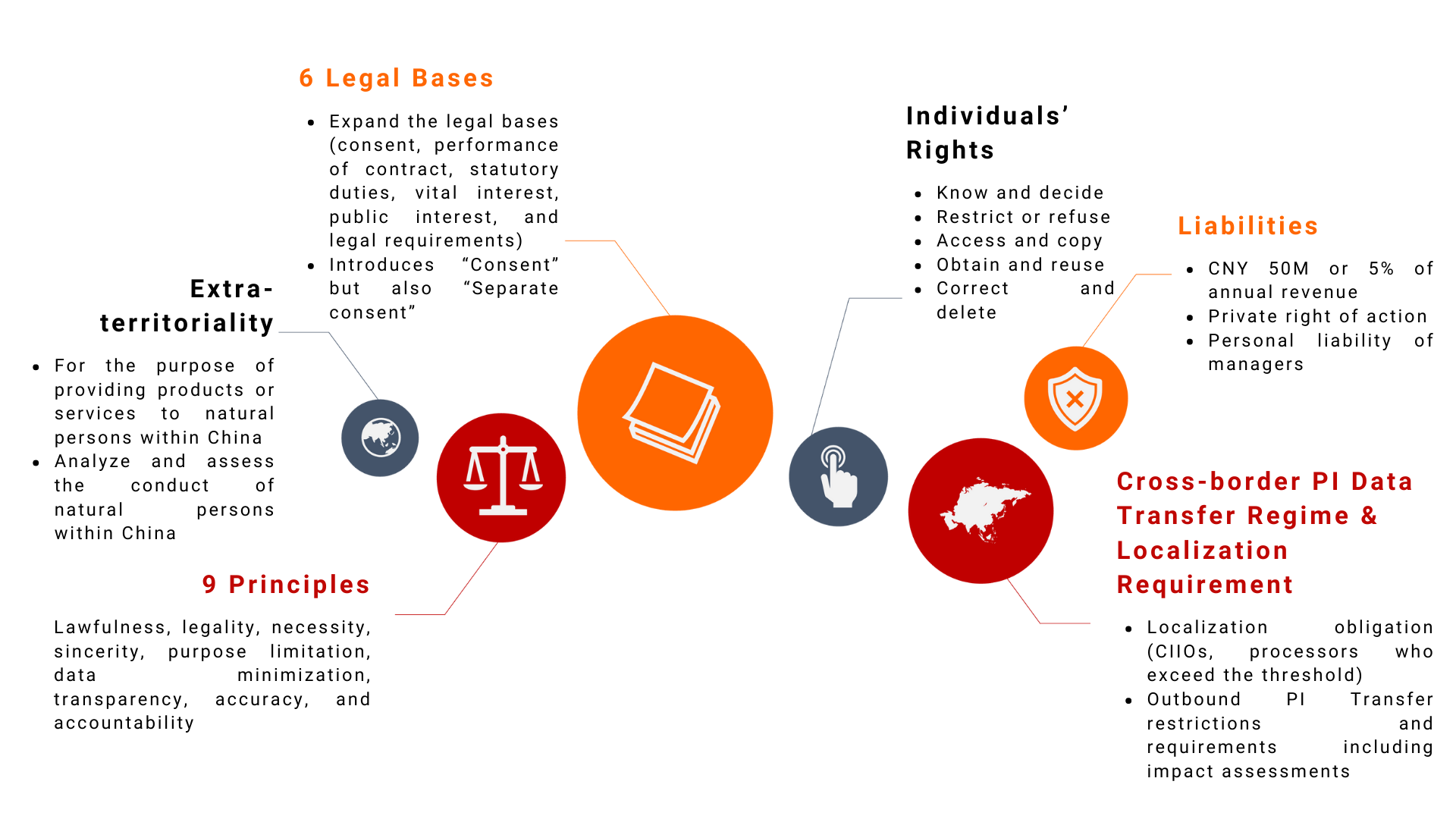
The PIPL
- Determination of Personal Information (“PI”)
- Basic Principles on PI processing
- Rights of PI Subjects
- Rules on Data Localization and Cross-border Transfer
- PI Processor Obligations .


Main novelties of the PIPL
Has your business to comply with the PIPL?
Like the EU GDPR, also the PIPL has extraterritorial application and imposes thought-through privacy management policies and practices to companies and entities all over the world, when the purpose of the processing is:
(i) To provide products or services to individuals in China
(ii) to “analyze” or “assess” the behaviour of individuals in China; and/or
(iii) for other purposes to be specified by laws and regulations
If you just discovered that your company falls in these conditions, you are also obliged to:
-
- establish a “dedicated office” in China, or
- appoint a “designated representative” in China, and
- liaise with the Cyberspace Administration of China (CAC) and other competent government authorities depending on your processing activities
PrivacyRules PIPL compliance package for international businesses
PrivacyRules has created an efficient and cost-effective package to assess your legal and technical obligations towards the PIPL, and to adopt the appropriate steps in order to continue operating with peace of mind and avoid hefty fines. Our package offers:
- PIPL legal assessment for compliance according to the new Chinese framework; and/or
- PIPL cybersecurity pre-assessment to pass the assessment of the Cyberspace Administration Authority of China (CAC); and/or
- PIPL-other national frameworks comparative assessment to ensure that your activities in China are also in compliance with your relevant national framework, especially in data transfer operations


What you get with our package
Upon its subscription, you will receive a wealth of informative material for your corporate awareness and for the education of your workforce, which is one of the most important initial steps to comply with the PIPL and to demonstrate to customers and partners that you have embraced the culture of care for personal data protection and cybersecurity.
Our package journey gives you:
-
- Planning and scoping, the identification of the boundaries and parameters for compliance
- Data mapping, compliance checklist and document review
- On-site or videocall assessment, to consolidate status quo knowledge
- Thorough analysis of info received on current posture
- Report delivery, based on which to plan tailor-made company compliance program